In my previous post, I discussed the adoption of Zero Trust/SASE architectures to address the new risks associated with a decentralized world where direct-to-cloud access renders perimeter gateways and VPN tools obsolete. Specifically, I discussed the critical need to bolster a ZT access strategy with web isolation capabilities when users, devices, browsers, and networks are beyond the reach of IT control.
Since then, we published a webinar with Chase Cunningham at Forrester, where we expanded on these topics and highlighted a key customer (US Navy) who has standardized on Silo to enable work-from-home access in rapid response to COVID-19. You can hear the full webinar and Q&A here.
In this post, I’ll be moving on from the “why” to consider the “how” web isolation can be combined with an identity & access management gateway or identity provider (IdP) to create a flexible and secure data delivery channel.
To implement a secure data delivery channel requires an understanding of the security context when applications are accessed, coupled with a method for conditionally invoking isolation based on that context.
The context refers to the specifics of the access scenario: who is the user?; where are they located?; what device/platform are they using?; is that platform compliant?; what app/data is being accessed? More sophisticated context definitions could include; what is the time of day or what behavioral patterns are observed.
Based on this context, the goal of zero trust/SASE solutions is to apply access control policies conditionally. This is where the combination of an identity provider (IdP) and Silo can significantly expand the range of access controls and data security options that organizations can enforce. IdPs are a logical control point -- they are always in-line regardless of device or location, and most modern solutions have support for context-based access controls.
Many identity and access management providers offer a variety of contextual hooks on which to tie access controls. For example:
An example of a composite policy resulting from these controls might say:
Grant access from IT managed devices that satisfy device posture and are within the corporate network. Require multi-factor auth if these same devices are accessing from off-network. Block access from unmanaged devices and non-compliant devices regardless of location.
We can even consider applying these rules for specific users, groups, and applications to add further granularity.
But as powerful as these rules are, they remain limited in scope when overlaid on specific real-world access scenarios. Consider organizations with some portion of loosely connected users for whom device identity, posture, and location are not applicable control hooks. Franchisee networks, contractor-heavy businesses, companies that leverage BPOs, or industries with highly remote/mobile workforces. In these situations, blocking access breaks business workflows, while allowing access can add unacceptable data risks. What’s needed is a finer-edged instrument to carve out these higher risk access scenarios and enforce a higher security access method.
As discussed in the last post, Silo’s web isolation platform brings holistic security to zero-trust access scenarios through full data isolation, policy control, and audit/visibility. Leveraging existing IdP control points, we can quickly stitch together both solutions to come up with a much more flexible access model.
Let’s re-consider the composite policy example from above, summarized in this table:
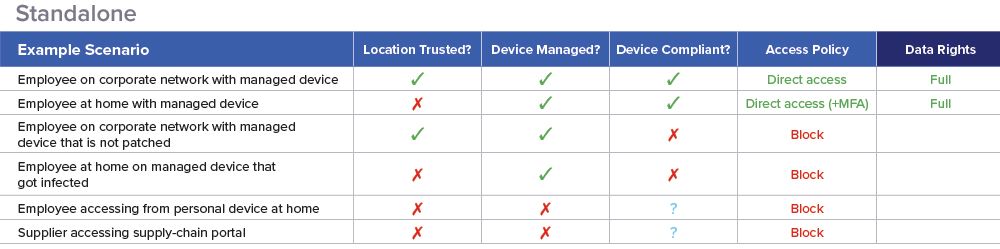
Source: Authentic8
Blocking access from unmanaged devices can start to look too restrictive when considering more arm's-length relationships with partners, suppliers, loosely coupled workforces, and even employees working from home. Similarly, for controlled users on managed devices, the device posture restriction might rub up against remote users who aren't always on VPN to receive real-time distributions of software updates and patches. All of these situations may require granting access for business reasons, but in a way that elevates security and control.
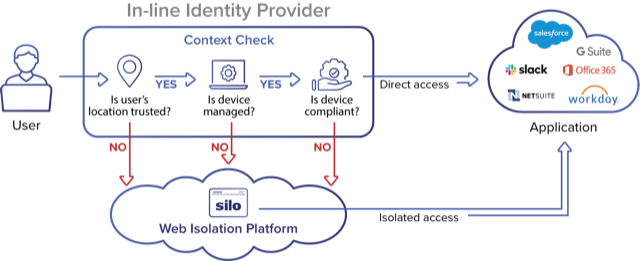
This is where web isolation through Silo can thread the needle. Configuring the identity gateway to include the Silo cloud in the list of trusted networks creates a secure access point regardless of other context details. Once this is in place, the organization is free to block direct access in different situations as needed (for example, from unknown networks, unmanaged or out-of-compliance devices).
This blended configuration seamlessly combines direct access in high-trust scenarios, with isolated/controlled access in low-trust scenarios. In these low-trust scenarios, Silo ensures that data is entirely air-gapped from local device and browser vulnerabilities, is governed by policies to prevent data leak and misuse, and is wrapped with logging analytics to oversee and audit user actions against the data.
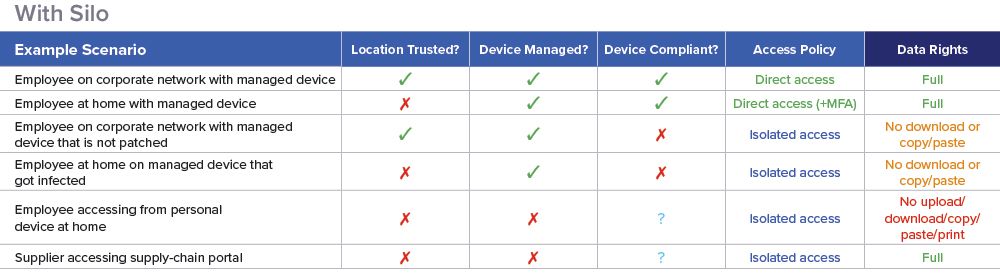
Source: Authentic8
Security-aware organizations are embracing ZT/SASE models for a reason. Diversity in users, devices, locations, apps, and data types are no longer exotic. And traditional access controls in the market are too blunt to meet this reality. Extending your identity gateway with secure delivery through web isolation allows companies to implement a much more dynamic service edge that flexes to fit real-world scenarios.